
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has identified eight flaws that are actively being exploited and has added them to the Known Exploited Vulnerabilities (KEV) catalog.
These flaws include six security vulnerabilities that have already been patched in Samsung mobile devices, as well as two vulnerabilities in D-Link routers and access points, which have also been patched. It’s important to note that all of these bugs have been patched for several years.
In November 2022, Google Project Zero revealed a series of vulnerabilities that were used as part of an exploit chain targeting Samsung phones. Here are the newly added vulnerabilities:
- CVE-2019-17621: D-Link DIR-859 Router Command Execution Vulnerability
- CVE-2019-20500: D-Link DWL-2600AP Access Point Command Injection Vulnerability
- CVE-2021-25487: Samsung Mobile Devices Out-of-Bounds Read Vulnerability
- CVE-2021-25489: Samsung Mobile Devices Improper Input Validation Vulnerability
- CVE-2021-25394: Samsung Mobile Devices Race Condition Vulnerability
- CVE-2021-25395: Samsung Mobile Devices Race Condition Vulnerability
- CVE-2021-25371: Samsung Mobile Devices Unspecified Vulnerability
- CVE-2021-25372: Samsung Mobile Devices Improper Boundary Check Vulnerability
The most severe vulnerability in Samsung devices is CVE-2021-25487, which is classified as an out-of-bounds read error in the handset modem interface driver. This vulnerability enables an attacker to run any code they choose.
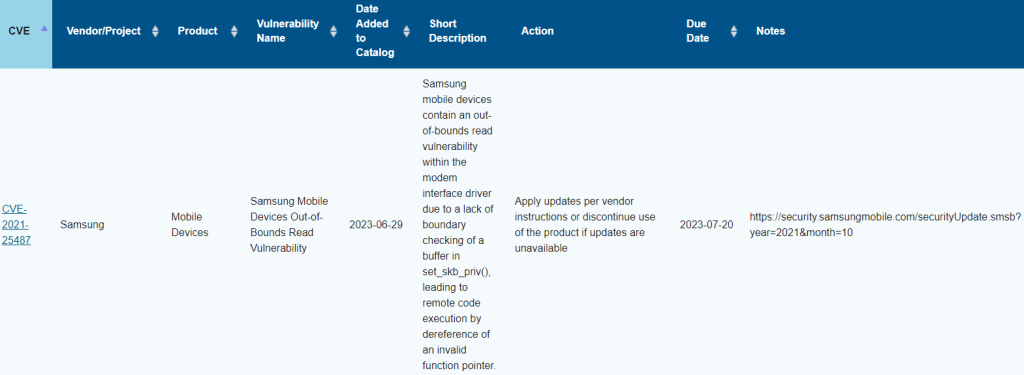
Both Samsung and the National Institute of Standards and Technology (NIST) have classified this vulnerability as “high severity,” with NIST giving it a CVSS score of 7.8 and Samsung rating it at 7.3.

Palo Alto Networks Unit 42 recently discovered that one of the D-Link vulnerabilities (CVE-2019-17621) is being exploited by a new variant of the Mirai botnet, targeting the D-Link DIR-859 router. This Mirai variant also targets vulnerabilities in Zyxel and Netgear devices.
Although it is not clear how the flaws in Samsung devices are being exploited, considering the specific targeting, it is possible that they are being used in highly targeted attacks by commercial spyware vendors.
In response to these active exploitations, Federal Civilian Executive Branch (FCEB) agencies must apply the necessary fixes to secure their networks against potential threats by July 20, 2023.
